¶ 一、背景
在高可用 Kubernetes 部署中,需要单独部署外部 etcd 集群,而不是使用 kubeadm 默认在 master 节点上部署的 etcd。以下是关于这一配置场景的详细记录。
¶ 二、etcd简介
etcd 是一个高可用的分布式键值存储系统,主要用于存储和管理配置信息、服务发现信息以及其他重要的元数据。etcd 是由 CoreOS 开发的,基于 Raft 共识算法来保证数据的一致性和可靠性。
¶ 2.1 etcd 关键特点
- 分布式:etcd 运行在多个节点上,通过 Raft 协议确保数据一致性。
- 高可用性:即使部分节点出现故障,etcd 也能继续提供服务。
- 一致性保证:使用 Raft 协议来确保数据的一致性,支持强一致性读写。
- 键值存储:数据以键值对的形式存储,适合存储配置和元数据。
- 支持事务:支持原子操作,如事务操作来保证数据的正确性。
¶ 2.2 etcd 主要功能
- 分布式键值存储:etcd 是一个高可用的分布式键值存储系统,支持高效的键值对存储和读取,并提供强一致性保证。
- 一致性保证:etcd 使用 Raft 协议确保数据一致性,即使部分节点故障,数据仍然保持一致。
- 高可用性:etcd 通过数据复制到多个节点提供高可用性和容错能力,只要大多数节点正常,数据依然可用。
- 事务支持:etcd 支持原子操作和事务,确保对多个键值对的更改安全一致。
- 观察和通知:etcd 支持事件监听和观察功能,客户端可以订阅键值变化,适合动态配置更新。
- 持久化存储:etcd 将数据持久化到磁盘,确保在节点重启或故障时数据不丢失。
- 分布式锁:etcd 提供分布式锁,支持节点间的协调和同步,常用于确保资源唯一性或任务协调。
- 范围查询:etcd 支持对键值对的范围查询,便于批量检索数据。
- API 接口:etcd 提供 HTTP/gRPC API,支持基本的 CRUD 操作、事务和观察功能。
这些功能使 etcd 成为一个强大且可靠的分布式键值存储系统,适合用于需要高一致性和高可用性的场景,特别是在 Kubernetes 这样的集群管理系统中。
¶ 2.3 etcd 在 Kubernetes 中使用场景
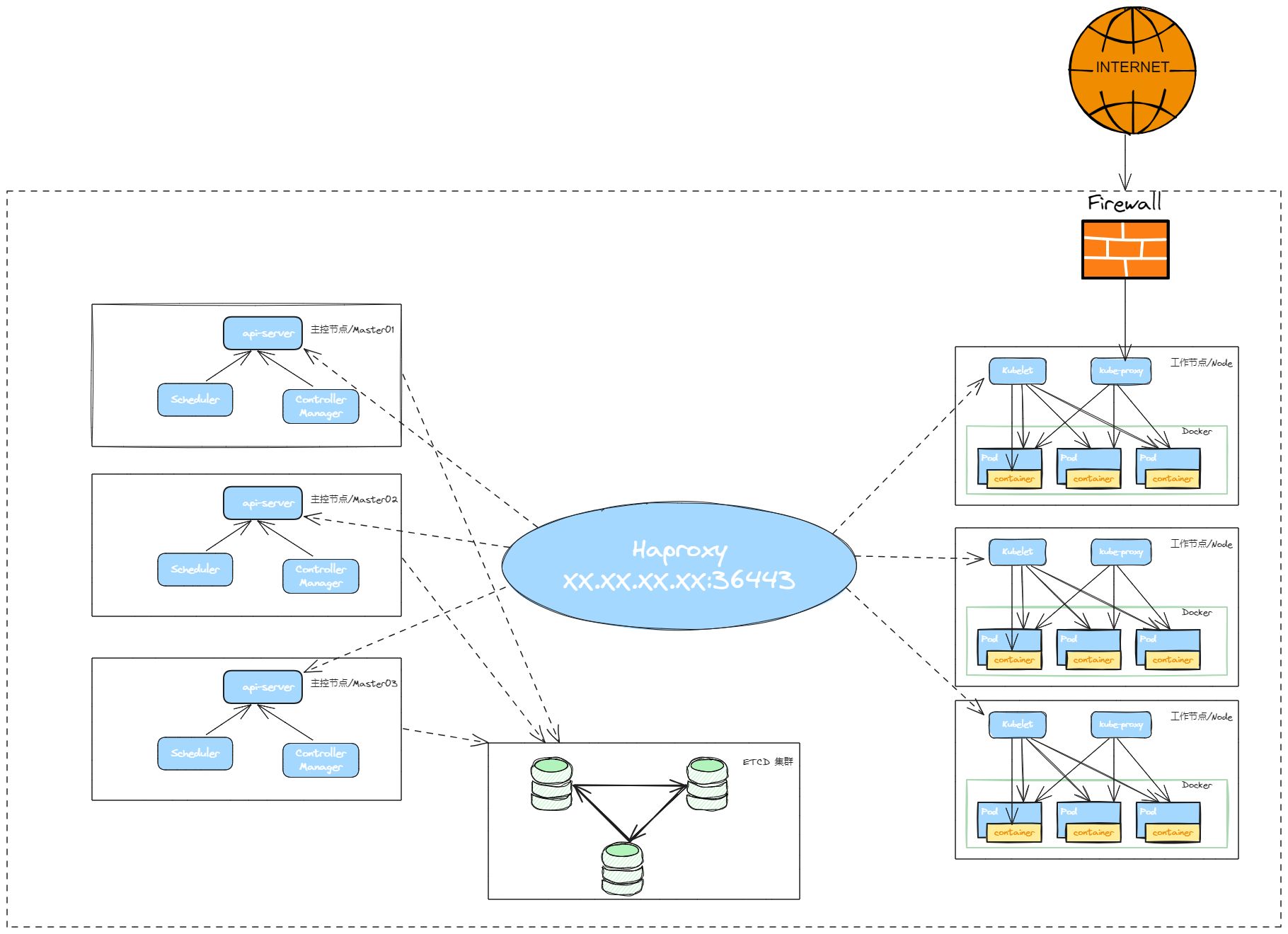
在 Kubernetes (K8S) 集群中,etcd 扮演着至关重要的角色。它主要用于存储和管理 Kubernetes 的所有集群状态信息和配置数据。以下是 etcd 在 Kubernetes 中的一些关键使用场景:
- 集群状态存储:Kubernetes 的所有集群状态、配置信息、资源定义等都存储在 etcd 中。包括 Pod、Service、ConfigMap、Secret 等对象的状态和配置都被存储在 etcd 中。
- 高可用性配置:提供高可用性和容错能力,保证即使在集群中的一些节点失效的情况下,Kubernetes 也能继续运行和提供服务。
- 数据一致性保证: 使用 Raft 协议确保数据的一致性,这对于 Kubernetes 来说是非常重要的,因为它需要确保所有操作和状态在集群中的一致性。
- 服务发现:Kubernetes 的服务发现机制依赖于 etcd 存储服务的状态和信息。etcd 记录服务的 IP 地址和端口信息,允许其他组件进行服务发现。
- 动态配置管理:Kubernetes 使用 etcd 来管理配置变化,比如部署新的应用版本或调整资源配置。etcd 的事务支持使得配置更改能够被安全地提交和应用。
- 审计和恢复:etcd 的持久化存储允许 Kubernetes 在发生故障或恢复操作时能够重建集群状态。etcd 的备份和恢复机制是确保 Kubernetes 集群数据安全的重要手段。
¶ 三、使用二进制方式部署etcd
- 参考官方文档:https://github.com/etcd-io/etcd/releases
- etcd 软件包下载地址: https://github.com/etcd-io/etcd/releases/download/v3.5.15/etcd-v3.5.15-linux-amd64.tar.gz
¶ 3.1 etcd单节点部署
¶ 3.1.1 环境准备
| 机器IP | 主机名 | etcd版本 |
|---|---|---|
| 172.22.33.223 | etcd | v3.3.8 |
¶ 3.1.2 下载软件包,创建etcd工作目录
- etcd 软件包下载地址: https://github.com/etcd-io/etcd/releases/download/v3.5.15/etcd-v3.5.15-linux-amd64.tar.gz
#创建etcd工作目录
$ mkdir -p /home/application/etcd/{bin,cfg,data,ssl}
# 下载软件包并解压
$ wget https://github.com/etcd-io/etcd/releases/download/v3.5.15/etcd-v3.5.15-linux-amd64.tar.gz
$ tar -xf etcd-v3.5.15-linux-amd64.tar.gz
$ mv etcd-v3.5.15-linux-amd64/{etcdctl,etcd} /home/application/etcd/bin/
#验证etcd版本
$ /home/application/etcd/bin/etcd --version
etcd Version: 3.5.15
Git SHA: 9a5533382
Go Version: go1.21.12
Go OS/Arch: linux/amd64
¶ 3.1.3 使用cfssl 工具签发etcd 证书
cfssl是一个用于生成和管理 TLS/SSL 证书的工具,专门设计用于处理公钥基础设施(PKI)操作。它由 Cloudflare 开发,提供了一个命令行工具和一个 API 服务,可以用来生成、签发和管理证书。
- cfssl 的主要功能包括:
- 生成证书签名请求(CSR): 生成包含公钥信息的文件,用于向证书颁发机构(CA)申请证书。
- 签发证书: 作为一个轻量级的证书颁发机构(CA),可以签发符合要求的证书。
- 生成自签名证书: 创建自签名的根证书(Root CA),用于内部系统的信任链。
- 证书管理: 包括查看、更新、撤销和续期证书的功能。
- 支持 JSON API: 提供 HTTP/JSON API,允许通过 RESTful 接口自动化证书管理操作。
- 使用场景
- 自建 CA: 在一些企业环境或开发环境中,使用 cfssl 自建 CA 系统,用于内部服务的证书管理。
- 自动化证书管理: 在 DevOps 环境中,通过 API 自动生成和更新证书。
- 安全的服务间通信: 在分布式系统中,为各个服务生成和分发 TLS 证书,保证服务间通信的安全性。
#下载cfssl 签发工具【可能背墙,自行备源】
[root@master1 ~]# curl -L https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 -o /usr/local/bin/cfssl
[root@master1 ~]# curl -L https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 -o /usr/local/bin/cfssljson
[root@master1 ~]# curl -L https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64 -o /usr/local/bin/cfssl-certinfo
[root@master1 ~]# chmod +x /usr/local/bin/cfssl*
- 签发证书-配置 CA 并创建 TLS 证书
创建 Certificate Authority(CA), 并为 etcd创建 TLS 证书。
# 切换到证书工作目录下
$ cd /home/application/etcd/ssl
# 配置 CA 的操作参数和策略。这些参数决定了 CA 的行为,如证书的有效期、证书链的深度、使用的加密算法等
$ cat << EOF | tee ca-config.json
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"etcd": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
EOF
# 配置CA 生成证书签名请求(CSR)
$ cat << EOF | tee ca-csr.json
{
"CN": "etcd CA",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Nanjing",
"ST": "Nanjing"
}
]
}
EOF
#生成 CA 凭证和私钥:
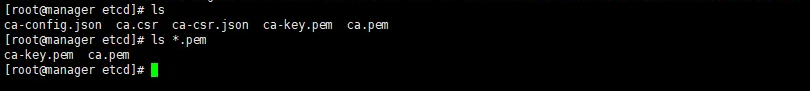
$ cfssl gencert -initca ca-csr.json | cfssljson -bare ca
#结果将生成以下两个文件:
$ ls -l ca*.pem
-rw------- 1 root root 1679 8月 26 14:19 ca-key.pem
-rw-r--r-- 1 root root 1265 8月 26 14:19 ca.pem
- 签发etcd server证书
# 创建etcd 证书请求文件,修改请求文件中hosts字段包含所有etcd节点IP
$ cat << EOF | tee server-csr.json
{
"CN": "etcd",
"hosts": [
"172.22.33.223"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Nanjing",
"ST": "Nanjing"
}
]
}
EOF
# 生成etcd server证书:
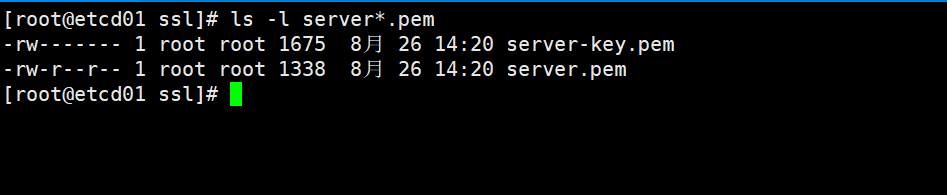
$ cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=etcd server-csr.json | cfssljson -bare server
#结果将生成以下两个文件:
$ ls -l server*.pem
-rw------- 1 root root 1675 8月 26 14:20 server-key.pem
-rw-r--r-- 1 root root 1338 8月 26 14:20 server.pem
¶ 3.1.4 创建配置文件
$ cd /home/application/etcd/cfg
$ cat >> /home/application/etcd/cfg/etcd.conf << EOF
#[Member]
#etcd 成员的名称,这是节点在集群中的唯一标识。
ETCD_NAME="etcd"
#etcd 数据的存储目录,这里我们自己定了一个数据路径
ETCD_DATA_DIR="/home/application/etcd/data/default.etcd"
#etcd 节点监听来自集群内其他节点的通信的地址和端口
ETCD_LISTEN_PEER_URLS="https://172.22.33.223:2380"
# 指定 etcd 实例实际监听的地址,等于 etcd 实例接收客户端请求的地址。
ETCD_LISTEN_CLIENT_URLS="https://172.22.33.223:2379,http://127.0.0.1:2379"
# 指定 etcd 实例对外公布的地址,客户端和其他 etcd 节点用来连接和访问 etcd 实例。
ETCD_ADVERTISE_CLIENT_URLS="https://172.22.33.223:2379,http://127.0.0.1:2379"
#同时支持V2 API
ETCD_ENABLE_V2="true"
#[Security]
ETCD_CERT_FILE="/home/application/etcd/ssl/server.pem"
ETCD_KEY_FILE="/home/application/etcd/ssl/server-key.pem"
ETCD_TRUSTED_CA_FILE="/home/application/etcd/ssl/ca.pem"
ETCD_CLIENT_CERT_AUTH="true"
ETCD_PEER_CERT_FILE="/home/application/etcd/ssl/server.pem"
ETCD_PEER_KEY_FILE="/home/application/etcd/ssl/server-key.pem"
ETCD_PEER_TRUSTED_CA_FILE="/home/application/etcd/ssl/ca.pem"
ETCD_PEER_CLIENT_CERT_AUTH="true"
EOF
¶ 3.1.5 创建etcd.service 文件
$ cat >> /usr/lib/systemd/system/etcd.service << EOF
[Unit]
Description=Etcd Server
After=network.target
After=network-online.target
Wants=network-online.target
[Service]
Type=notify
EnvironmentFile=/home/application/etcd/cfg/etcd.conf
ExecStart=/home/application/etcd/bin/etcd
Restart=on-failure
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
EOF
¶ 3.1.6 启动etcd
$ systemctl daemon-reload
$ systemctl enable etcd
$ systemctl start etcd
# 检查etcd 服务是否正常
$ ps -ef | grep etcd | grep -v grep
root 7885 1 0 15:23 ? 00:00:00 /home/application/etcd/bin/etcd
¶ 3.1.7etcd 服务可用性测试
使用etcdctl 工具测试,模拟写入数据,验证数据; etcdctl 工具,在安装包里有提供
#使用 etcdctl 工具快速检查指定的 etcd 节点(或节点集)的健康状态
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
--write-out=table endpoint health
+----------------------------+--------+-------------+-------+
| ENDPOINT | HEALTH | TOOK | ERROR |
+----------------------------+--------+-------------+-------+
| https://172.22.33.223:2379 | true | 17.746218ms | |
+----------------------------+--------+-------------+-------+
#使用 etcdctl 工具查看指定 etcd 节点(或节点集)当前的详细状态信息
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
--write-out=table endpoint status
+----------------------------+------------------+---------+---------+-----------+------------+-----------+------------+--------------------+--------+
| ENDPOINT | ID | VERSION | DB SIZE | IS LEADER | IS LEARNER | RAFT TERM | RAFT INDEX | RAFT APPLIED INDEX | ERRORS |
+----------------------------+------------------+---------+---------+-----------+------------+-----------+------------+--------------------+--------+
| https://172.22.33.223:2379 | 8e9e05c52164694d | 3.5.15 | 20 kB | true | false | 2 | 5 | 5 | |
+----------------------------+------------------+---------+---------+-----------+------------+-----------+------------+--------------------+--------+
#使用 etcdctl 工具验证测试 member
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
--write-out=table member list
--write-out=table member list
+------------------+---------+------+-----------------------+--------------------------------------------------+------------+
| ID | STATUS | NAME | PEER ADDRS | CLIENT ADDRS | IS LEARNER |
+------------------+---------+------+-----------------------+--------------------------------------------------+------------+
| 8e9e05c52164694d | started | etcd | http://localhost:2380 | http://127.0.0.1:2379,https://172.22.33.223:2379 | false |
+------------------+---------+------+-----------------------+--------------------------------------------------+------------+
# etcdctl 工具验证测试数据读写
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
put srebro.cn hello
OK
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
get srebro.cn
srebro.cn
hello
¶ 3.2 etcd集群部署
¶ 3.2.1 环境准备
| 机器IP | 主机名 | etcd版本 |
|---|---|---|
| 172.22.33.223 | etcd-01 | v3.3.8 |
| 172.22.33.224 | etcd-02 | v3.3.8 |
| 172.22.33.225 | etcd-03 | v3.3.8 |
¶ 3.2.2 修改主机名,添加hosts解析
在每台主机上执行
设置主机名:
$ hostnamectl set-hostname etcd-01
$ hostnamectl set-hostname etcd-02
$ hostnamectl set-hostname etcd-03
#在所有节点添加hosts:
$ cat >> /etc/hosts << EOF
172.22.33.223 etcd-01
172.22.33.224 etcd-02
172.22.33.225 etcd-03
EOF
¶ 3.2.3 下载软件包,创建etcd工作目录
在每台主机上执行
- etcd 软件包下载地址: https://github.com/etcd-io/etcd/releases/download/v3.5.15/etcd-v3.5.15-linux-amd64.tar.gz
#创建etcd工作目录
$ mkdir -p /home/application/etcd/{bin,cfg,data,ssl}
# 下载软件包并解压
$ wget https://github.com/etcd-io/etcd/releases/download/v3.5.15/etcd-v3.5.15-linux-amd64.tar.gz
$ tar -xf etcd-v3.5.15-linux-amd64.tar.gz
$ mv etcd-v3.5.15-linux-amd64/{etcdctl,etcd} /home/application/etcd/bin/
#验证etcd版本
$ /home/application/etcd/bin/etcd --version
etcd Version: 3.5.15
Git SHA: 9a5533382
Go Version: go1.21.12
Go OS/Arch: linux/amd64
¶ 3.2.4 使用cfssl 工具签发etcd 证书
在172.22.33.223 主机上执行
签发证书的动作只需要在一台服务器上完成,签发之后,拷贝证书即可
#下载cfssl 签发工具【可能背墙,自行备源】
[root@master1 ~]# curl -L https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 -o /usr/local/bin/cfssl
[root@master1 ~]# curl -L https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 -o /usr/local/bin/cfssljson
[root@master1 ~]# curl -L https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64 -o /usr/local/bin/cfssl-certinfo
[root@master1 ~]# chmod +x /usr/local/bin/cfssl*
- 签发证书-配置 CA 并创建 TLS 证书
创建 Certificate Authority(CA), 并为 etcd创建 TLS 证书。
# 切换到证书工作目录下
$ cd /home/application/etcd/ssl
# 配置 CA 的操作参数和策略。这些参数决定了 CA 的行为,如证书的有效期、证书链的深度、使用的加密算法等
$ cat << EOF | tee ca-config.json
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"etcd": {
"expiry": "87600h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
EOF
# 配置CA 生成证书签名请求(CSR)
$ cat << EOF | tee ca-csr.json
{
"CN": "etcd CA",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Nanjing",
"ST": "Nanjing"
}
]
}
EOF
#生成 CA 凭证和私钥:
$ cfssl gencert -initca ca-csr.json | cfssljson -bare ca
#结果将生成以下两个文件:
$ ls -l ca*.pem
-rw------- 1 root root 1679 8月 26 14:19 ca-key.pem
-rw-r--r-- 1 root root 1265 8月 26 14:19 ca.pem
- 签发etcd server证书
修改请求文件中hosts字段包含所有etcd节点IP,172.22.33.223,172.22.33.224 ,172.22.33.225
# 创建etcd 证书请求文件
$ cat << EOF | tee server-csr.json
{
"CN": "etcd",
"hosts": [
"172.22.33.223",
"172.22.33.224",
"172.22.33.225"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Nanjing",
"ST": "Nanjing"
}
]
}
EOF
# 生成etcd server证书:
$ cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=etcd server-csr.json | cfssljson -bare server
#结果将生成以下两个文件:
$ ls -l server*.pem
-rw------- 1 root root 1675 8月 26 14:20 server-key.pem
-rw-r--r-- 1 root root 1338 8月 26 14:20 server.pem
- 同步etcd 证书到其他节点
scp -rp /home/application/etcd/ssl/* 172.22.33.224:/home/application/etcd/ssl/*
scp -rp /home/application/etcd/ssl/* 172.22.33.225:/home/application/etcd/ssl/*
¶ 3.2.5 创建配置文件
172.22.33.223 etcd-01 节点
$ cd /home/application/etcd/cfg
$ cat >> /home/application/etcd/cfg/etcd.conf << EOF
#[Member]
ETCD_NAME="etcd01"
ETCD_DATA_DIR="/home/application/etcd/data/default.etcd"
ETCD_LISTEN_PEER_URLS="https://172.22.33.223:2380"
ETCD_LISTEN_CLIENT_URLS="https://172.22.33.223:2379,http://127.0.0.1:2379"
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://172.22.33.223:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://172.22.33.223:2379"
ETCD_INITIAL_CLUSTER="etcd01=https://172.22.33.223:2380,etcd02=https://172.22.33.224:2380,etcd03=https://172.22.33.225:2380"
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"
ETCD_INITIAL_CLUSTER_STATE="new"
ETCD_ENABLE_V2="true"
#[Security]
ETCD_CERT_FILE="/home/application/etcd/ssl/server.pem"
ETCD_KEY_FILE="/home/application/etcd/ssl/server-key.pem"
ETCD_TRUSTED_CA_FILE="/home/application/etcd/ssl/ca.pem"
ETCD_CLIENT_CERT_AUTH="true"
ETCD_PEER_CERT_FILE="/home/application/etcd/ssl/server.pem"
ETCD_PEER_KEY_FILE="/home/application/etcd/ssl/server-key.pem"
ETCD_PEER_TRUSTED_CA_FILE="/home/application/etcd/ssl/ca.pem"
ETCD_PEER_CLIENT_CERT_AUTH="true"
EOF
172.22.33.224 etcd-02 节点
#[Member]
ETCD_NAME="etcd02"
ETCD_DATA_DIR="/home/application/etcd/data/default.etcd"
ETCD_LISTEN_PEER_URLS="https://172.22.33.224:2380"
ETCD_LISTEN_CLIENT_URLS="https://172.22.33.224:2379,http://127.0.0.1:2379"
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://172.22.33.224:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://172.22.33.224:2379"
ETCD_INITIAL_CLUSTER="etcd01=https://172.22.33.223:2380,etcd02=https://172.22.33.224:2380,etcd03=https://172.22.33.225:2380"
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"
ETCD_INITIAL_CLUSTER_STATE="new"
ETCD_ENABLE_V2="true"
#[Security]
ETCD_CERT_FILE="/home/application/etcd/ssl/server.pem"
ETCD_KEY_FILE="/home/application/etcd/ssl/server-key.pem"
ETCD_TRUSTED_CA_FILE="/home/application/etcd/ssl/ca.pem"
ETCD_CLIENT_CERT_AUTH="true"
ETCD_PEER_CERT_FILE="/home/application/etcd/ssl/server.pem"
ETCD_PEER_KEY_FILE="/home/application/etcd/ssl/server-key.pem"
ETCD_PEER_TRUSTED_CA_FILE="/home/application/etcd/ssl/ca.pem"
ETCD_PEER_CLIENT_CERT_AUTH="true"
EOF
172.22.33.225 etcd-03 节点
#[Member]
ETCD_NAME="etcd03"
ETCD_DATA_DIR="/home/application/etcd/data/default.etcd"
ETCD_LISTEN_PEER_URLS="https://172.22.33.225:2380"
ETCD_LISTEN_CLIENT_URLS="https://172.22.33.225:2379,http://127.0.0.1:2379"
#[Clustering]
ETCD_INITIAL_ADVERTISE_PEER_URLS="https://172.22.33.225:2380"
ETCD_ADVERTISE_CLIENT_URLS="https://172.22.33.225:2379"
ETCD_INITIAL_CLUSTER="etcd01=https://172.22.33.223:2380,etcd02=https://172.22.33.224:2380,etcd03=https://172.22.33.225:2380"
ETCD_INITIAL_CLUSTER_TOKEN="etcd-cluster"
ETCD_INITIAL_CLUSTER_STATE="new"
ETCD_ENABLE_V2="true"
#[Security]
ETCD_CERT_FILE="/home/application/etcd/ssl/server.pem"
ETCD_KEY_FILE="/home/application/etcd/ssl/server-key.pem"
ETCD_TRUSTED_CA_FILE="/home/application/etcd/ssl/ca.pem"
ETCD_CLIENT_CERT_AUTH="true"
ETCD_PEER_CERT_FILE="/home/application/etcd/ssl/server.pem"
ETCD_PEER_KEY_FILE="/home/application/etcd/ssl/server-key.pem"
ETCD_PEER_TRUSTED_CA_FILE="/home/application/etcd/ssl/ca.pem"
ETCD_PEER_CLIENT_CERT_AUTH="true"
EOF
¶ 3.2.6 创建etcd.service 文件
在每台主机上执行
$ cat >> /usr/lib/systemd/system/etcd.service << EOF
[Unit]
Description=Etcd Server
After=network.target
After=network-online.target
Wants=network-online.target
[Service]
Type=notify
EnvironmentFile=/home/application/etcd/cfg/etcd.conf
ExecStart=/home/application/etcd/bin/etcd
Restart=on-failure
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
EOF
¶ 3.2.7 启动etcd
在每台主机上执行
$ systemctl daemon-reload
$ systemctl enable etcd
$ systemctl start etcd
# 检查etcd 服务是否正常
$ ps -ef | grep etcd | grep -v grep
root 7885 1 0 15:23 ? 00:00:00 /home/application/etcd/bin/etcd
¶ 3.2.8 etcd 集群服务可用性测试
使用etcdctl 工具测试,模拟写入数据,验证数据; etcdctl 工具,在安装包里有提供
#使用 etcdctl 工具快速检查指定的 etcd 节点(或节点集)的健康状态
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379,https://172.22.33.224:2379,https://172.22.33.225:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
--write-out=table endpoint health
+----------------------------+--------+-------------+-------+
| ENDPOINT | HEALTH | TOOK | ERROR |
+----------------------------+--------+-------------+-------+
| https://172.22.33.224:2379 | true | 16.120369ms | |
| https://172.22.33.223:2379 | true | 16.605784ms | |
| https://172.22.33.225:2379 | true | 19.851873ms | |
+----------------------------+--------+-------------+-------+
#使用 etcdctl 工具查看指定 etcd 节点(或节点集)当前的详细状态信息
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379,https://172.22.33.224:2379,https://172.22.33.225:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
--write-out=table endpoint status
+----------------------------+------------------+---------+---------+-----------+------------+-----------+------------+--------------------+--------+
| ENDPOINT | ID | VERSION | DB SIZE | IS LEADER | IS LEARNER | RAFT TERM | RAFT INDEX | RAFT APPLIED INDEX | ERRORS |
+----------------------------+------------------+---------+---------+-----------+------------+-----------+------------+--------------------+--------+
| https://172.22.33.223:2379 | b905915d4c303d2 | 3.5.15 | 20 kB | false | false | 2 | 11 | 11 | |
| https://172.22.33.224:2379 | 912027a2ec294592 | 3.5.15 | 20 kB | true | false | 2 | 11 | 11 | |
| https://172.22.33.225:2379 | 81330706eb2302ba | 3.5.15 | 20 kB | false | false | 2 | 11 | 11 | |
+----------------------------+------------------+---------+---------+-----------+------------+-----------+------------+--------------------+--------+
#使用 etcdctl 工具验证测试 member
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379,https://172.22.33.224:2379,https://172.22.33.225:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
--write-out=table member list
+------------------+---------+--------+----------------------------+----------------------------+------------+
| ID | STATUS | NAME | PEER ADDRS | CLIENT ADDRS | IS LEARNER |
+------------------+---------+--------+----------------------------+----------------------------+------------+
| b905915d4c303d2 | started | etcd01 | https://172.22.33.223:2380 | https://172.22.33.223:2379 | false |
| 81330706eb2302ba | started | etcd03 | https://172.22.33.225:2380 | https://172.22.33.225:2379 | false |
| 912027a2ec294592 | started | etcd02 | https://172.22.33.224:2380 | https://172.22.33.224:2379 | false |
+------------------+---------+--------+----------------------------+----------------------------+------------+
# etcdctl 工具验证测试数据读写
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379,https://172.22.33.224:2379,https://172.22.33.225:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
put srebro.cn hi
OK
$ /home/application/etcd/bin/etcdctl --endpoints=https://172.22.33.223:2379,https://172.22.33.224:2379,https://172.22.33.225:2379 \
--cacert=/home/application/etcd/ssl/ca.pem \
--cert=/home/application/etcd/ssl/server.pem \
--key=/home/application/etcd/ssl/server-key.pem \
get srebro.cn
srebro.cn
OK
¶ 四、kubeadm 使用集群外etcd,部署K8S集群
kubeadm 安装过程省略,直接贴上kubeadm-init.yaml 配置文件;主要查看etcd 那块的配置;
另外需要注意,ETCD 集群 与 apiservice 之间通信,是否采用TLS 加密,我上面部署的etcd集群实则是没有采用TLS 加密的
apiVersion: kubeadm.k8s.io/v1beta3
bootstrapTokens:
- groups:
- system:bootstrappers:kubeadm:default-node-token
token: 35sesk.5tm3tqc66tzlse8c
ttl: 24h0m0s
usages:
- signing
- authentication
kind: InitConfiguration
localAPIEndpoint:
advertiseAddress: 172.22.33.220
bindPort: 6443
nodeRegistration:
criSocket: unix:///var/run/cri-dockerd.sock
imagePullPolicy: IfNotPresent
name: k8s-master01
taints:
- effect: NoSchedule
key: node-role.kubernetes.io/master
---
apiServer:
certSANs:
- kubernetes
- kubernetes.default
- kubernetes.default.svc
- kubernetes.default.svc.cluster.local
- 172.22.33.220
- 112.11.11.11
- k8s.srebro.cn
timeoutForControlPlane: 4m0s
apiVersion: kubeadm.k8s.io/v1beta3
certificatesDir: /etc/kubernetes/pki
clusterName: kubernetes
controlPlaneEndpoint: 172.22.33.220:6443
controllerManager: {}
dns: {}
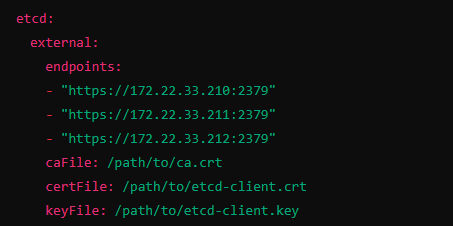
etcd:
external:
endpoints:
- "http://172.22.33.210:2379"
- "http://172.22.33.211:2379"
- "http://172.22.33.212:2379"
imageRepository: registry.aliyuncs.com/google_containers
kind: ClusterConfiguration
kubernetesVersion: v1.24.9
networking:
dnsDomain: cluster.local
podSubnet: 10.244.0.0/16
serviceSubnet: 10.96.0.0/12
scheduler: {}
- 不使用TLS 加密 ,需要配置如下内容:

- 如果需要使用TLS 加密 ,需要配置如下内容: